Quantum Cryptography: Secure Communication in Future
Imagine a world in which all your private messages, financial transactions, and sensitive data are perfectly secure against any hacking attempts. This is the promise of quantum cryptography—a high-tech field that uses principles of quantum mechanics to protect information. Let’s look into what quantum cryptography is, how it works, its real-world applications, and the challenges it faces in a way that’s easy to understand.
What Is Quantum Cryptography?
Quantum cryptography is the process of securing communication using the laws of quantum mechanics, which are the basic rules governing the behavior of particles at the smallest scales. Unlike traditional encryption methods, which rely on very complex mathematical algorithms, quantum cryptography uses the unique properties of quantum particles to create secure communication channels.
Anecdote: You are passing notes in class, and you have a special kind of paper that changes color if anyone tries to read it before it reaches your friend. Quantum cryptography works similarly; it ensures that if someone tries to eavesdrop on your message, the very act of spying changes the message, alerting you to the intrusion.
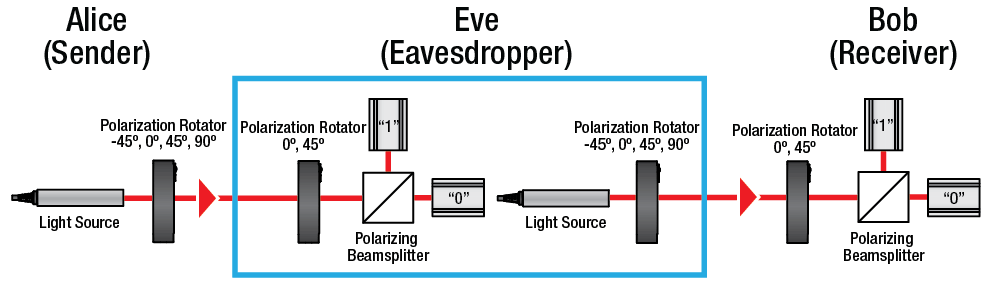
How Does Quantum Cryptography Work?
The best-known application of quantum cryptography is Quantum Key Distribution, specifically the BB84 protocol. Here’s a simplified explanation:
- Key Generation: Two parties, traditionally named Alice and Bob, want to share a secret key. Alice sends Bob a series of photons (tiny particles of light), each polarized in a specific direction. These polarizations represent bits (0s and 1s).
- Measurement: Bob measures the incoming photons using randomly chosen polarization filters. Due to the principles of quantum mechanics, measurement changes the state of photons, and Bob’s results will match Alice’s polarizations only sometimes.
- Key Sifting: Alice and Bob publicly compare notes on which measurements were made using the same polarization filters without revealing the actual results. They discard the bits where their filters didn’t match, leaving them with a shared sequence of bits—the secret key.
- Eavesdropping Check: If an eavesdropper (Eve) tries to intercept the photons, the act of measuring them will disturb their states, introducing errors that Alice and Bob can detect. If the error rate is too high, they know the key has been compromised and can abort the communication.
This process ensures that any attempt to eavesdrop on the key exchange is detectable, thus making the communication secure.
Real-Life Implementation of Quantum Cryptography
Quantum cryptography is shifting from theoretical research into practical applications:
- Financial Transactions: Banks and other financial institutions are exploring QKD to secure transactions. It protects against future threats from quantum computers that might break traditional encryption.
- Government Communications: Governments are interested in quantum cryptography to ensure the confidentiality of sensitive communications. National security information, for instance, needs to remain confidential.
- Healthcare Data: Quantum encryption allows protection of patient records against snooping and ensures adherence to regulatory compliance.
- Anecdote: During a national election in Switzerland, the vote counts in 2007 were sent quantum-cryptographically so as not to breach the security measures that protect democratic integrity in its election processes.
Challenges and Limitations
While quantum cryptography offers the potential, it comes with some limitations and challenges that must be addressed.
- Technical Complexity: Installation of QKD necessitates specialized equipment, including the single-photon sources and detectors that are still both expensive and fragile.
- Distance Limitation: Sending quantum keys without loss or decoherence can be hard over long distances, and a quantum repeater is still under development, which may extend the distances but still is under technological development.
- Integration with Existing Systems: The integration of quantum cryptographic methods into current communication infrastructures would require some changes and standardization in the systems.
- Security Assumptions: QKD is theoretically unbreakable, but for practical implementations, it is expected that the hardware and software used are free from vulnerability.
The solution to the above challenges is essential in the widespread adoption of quantum cryptography.
Conclusion: The Future of Quantum Cryptography
Quantum cryptography is expected to become more practical and wide-spread as technology progresses.
- Advancements in Technology: Ongoing research is leading to more robust and cost-effective quantum communication devices, bringing us closer to integrating quantum cryptography into everyday use.
- Standardization Efforts: Organizations like the National Institute of Standards and Technology (NIST) are working on developing standards for quantum-resistant cryptographic algorithms, preparing for a future where quantum computers are prevalent.
- Increased Security Needs: With the rise of cyber threats, the demand for unbreakable encryption methods is growing, making quantum cryptography an attractive solution for securing data in the quantum era.
Anecdote: In 2016, China launched the world’s first quantum communication satellite, “Micius,” successfully conducting QKD between ground stations over 1,200 kilometers apart. This achievement marked a significant milestone in the quest for global-scale quantum-secured communication.
Conclusion
Quantum cryptography is a new method of securing communication using the principles of quantum mechanics. It offers a revolutionary way of securing communication at a level that has not been seen before. It’s a promising field with benefits that make it so worth pursuing in the future. Being a high school student, learning the basics of quantum cryptography will give you an insight into a really fascinating area of physics, which will prepare you for the changing landscape of technology and cybersecurity.
